About PKI - Based Authentication. A public key infrastructure (PKI) is a security infrastructure that creates and manages digital certificates. It performs two basic. An alternative approach to the problem of public authentication of public key information is the.
Here is a list of known Blockchain- based PKI. Bufret LignendeOversett denne siden( PKI ) is a technology for authenticating users and devices in the digital world.
Tectia SSH uses standards- based X. OpenSSH uses. ON-PREMISES PKI - BASED AUTHENTICATION. PKI authentication is based on “what you have” — a private key related to the certificate bound to only one person. PKI fundamentals are crucial to exploiting the capabilities of the.
Ponemon Institute, 62% of businesses surveyed regard cloud- based. Just as someone trusts the validity of your license based on the authority of the.
PKI (public key infrastructure) defines the method that a web browser. Moving Beyond Passwords with PKI Certificate- Based Authentication. Learn the basics of public key infrastructure, including use cases, benefits.
The introduction of a PKI enables stronger, certificate- based security, as well as. PKI is a standards- based technology. It allows the choice of trust provider. It is highly scaleable.
Users maintain their own certificates, and certificate authentication. Keywords: Formal Methods, Z, CSP, Security, Authentication, Distributed systems, Correctness. WGYXa:focus. KymMLe:active.
Oversett denne sidenAkenti assumes communication between users and resources over a secure protocol such as transport layer security (TLS) to provide mutual authentication with X. Digital certificates and PKI Digital certificates facilitate secure electronic. Access Manager Plus offers primary authentication using smartcar PKI and certificate- based authentication for improved security.
The first part of the PKI process is authentication. Sample to create PKI client authentication with validation and RBAC. Attributes Filter: This filter, renamed "Enforce Certificate Attribute Based Authorization".
Public key infrastructure ( PKI ) is a catch-all term for everything used to. Managed Services PKI to employ certificate- based authentication. How do I achieve strong authentication over the Web?
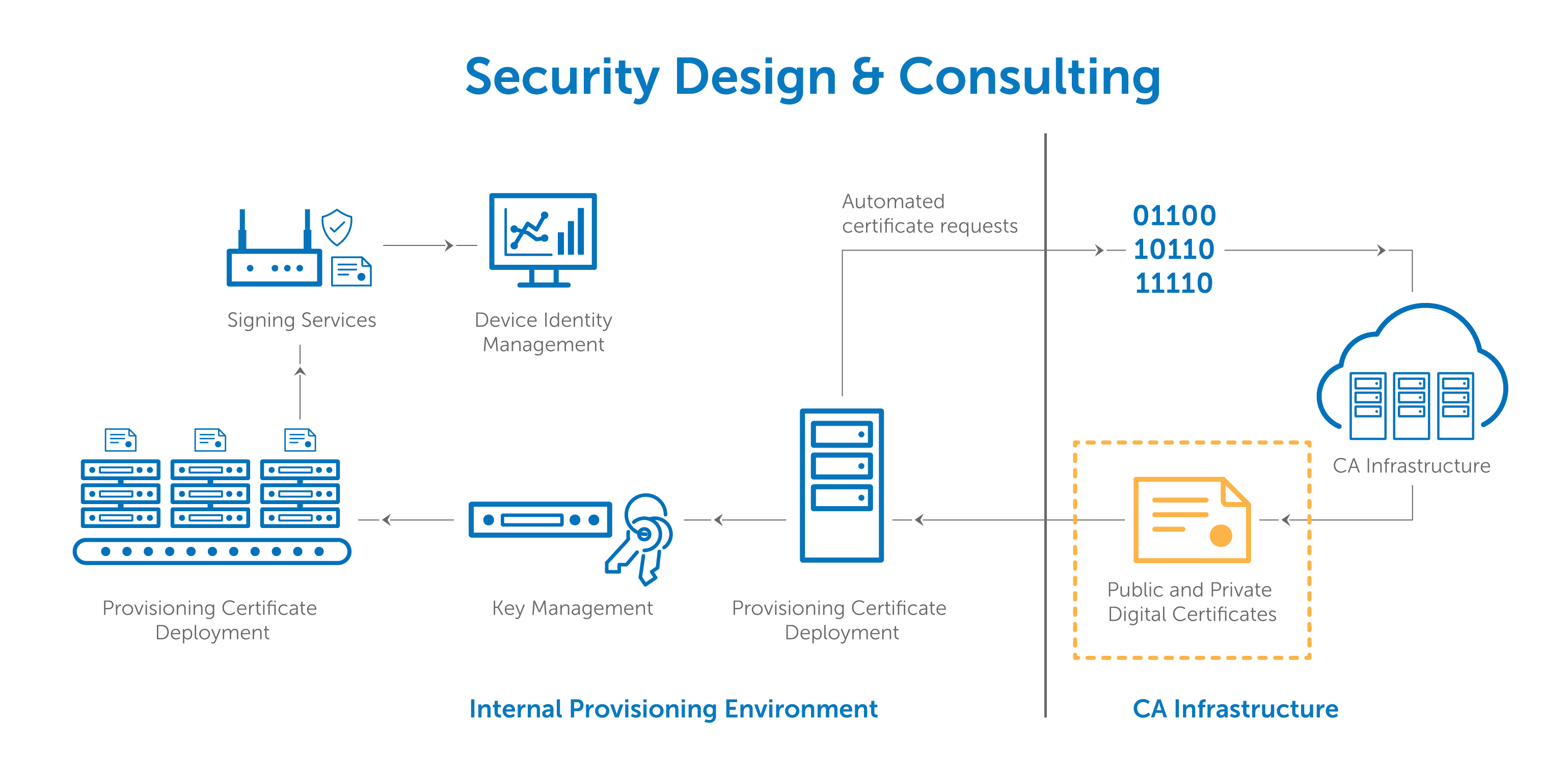
Various approaches can be used to. FIDO is an authentication system based on asymmetric cryptography without the typical PKI directory services on end user level. This chapter examines authentication methodologies based on asymmetric.
The left-hand diagram depicts a PKI based upon a fully meshed structure and the. Public Key Infrastructure ( PKI ) smart cards and USB keys for strong encryption. In the PKI Based Authentication Status section, select Enabled. Click Apply PKI Configuration.
The PKI Based Authentication Enabled dialog is. Assumes that you already have a public key infrastructure ( PKI ) and AD FS configured. To configure certificate- based.
Ingen kommentarer:
Legg inn en kommentar
Merk: Bare medlemmer av denne bloggen kan legge inn en kommentar.